
I recently applied for a project on a freelancing portal. They asked to invite me to the GitHub repo. The project is dense and had many files, after running the NullVoid scan it found malicious hidden code designed to steal cryptocurrency. This all stems to the recent NPM supply chain attacks. Thats what got me curious about this. Apparently these are connected to the criminal-syndicate Lazarus and these attacks are coming out of North Korea 🇰🇵.
So I decided to create a malware scanner for malicious obfuscated code detection for these exact malicious attacks.
NullVoid
🔗 https://github.com/kurt-grung/NullVoid
🔗 https://www.npmjs.com/package/nullvoid
NullVoid Scan
nullvoid scan
⠋ 🔍 Scanning ...
📁 auth.js (detected: OBFUSCATED_CODE, SUSPICIOUS_MODULE, MALICIOUS_CODE_STRUCTURE)
✔ ✅ Scan completed
🔍 NullVoid Scan Results
⚠️ 2 high-severity threat(s) detected:
1. MALICIOUS_CODE_STRUCTURE: Code structure indicates malicious obfuscated content
Package: /Users/kurtgrung/Desktop/FE/server/routes/api/auth.js
Line: 57
Sample: module.exports = router; ...
Severity: CRITICAL
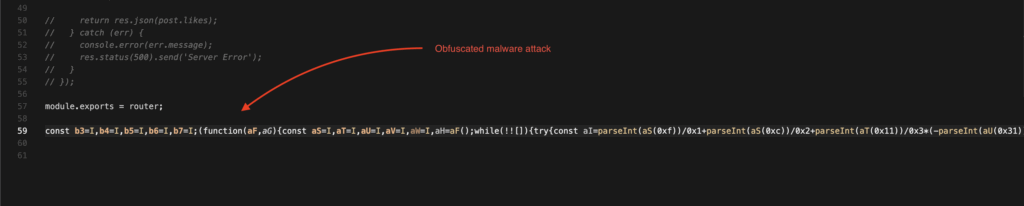
Details: MALICIOUS CODE DETECTED: Variable name mangling detected (2 instances). Massive obfuscated code blob detected (5681 characters). Hex encoding arrays detected (9 instances). Anti-debugging patterns detected. Code appended to legitimate module.exports detected. High entropy detected (5.52). Confidence: 130%
2. SUSPICIOUS_MODULE: Suspicious module require: fs
Package: /Users/kurtgrung/Desktop/FE/server/routes/api/auth.js
Severity: CRITICAL
Details: Code requires suspicious module: fs
📁 Directory Structure:
61 directories: client, server
309 files: README.md, client/README.md, client/package.json, client/public/favicon.ico, client/public/img/bat.jpg...
📊 Dependency Tree Analysis:
Total packages scanned: 0
Max depth reached: 0
Packages with threats: 0
Deep dependencies (depth ≥2): 0
📊 Scanned 1 directory(s), 181 file(s) in 1966ms
📁 auth.js (detected: OBFUSCATED_CODE, SUSPICIOUS_MODULE, MALICIOUS_CODE_STRUCTURE)
It found the malicious code hidden inside the `auth.js`
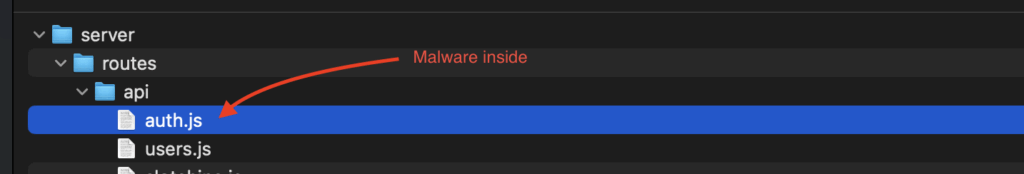
Hidden malware when reviewing the code will be hard to spot this!
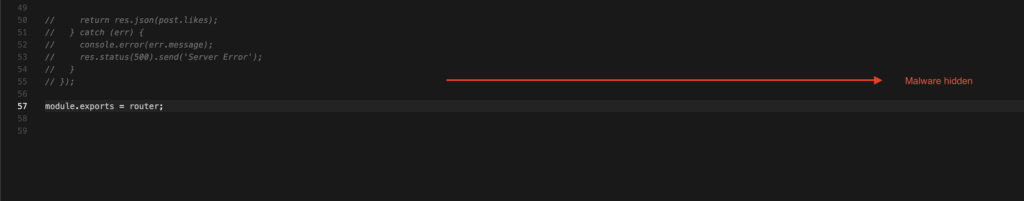
Hidden code uncovered
BitDefender picked it up as “Generic.LazarusScam.A.73D6628A”
https://defensestorm.com/insights/from-job-offer-to-cyber-threat-inside-the-lazarus-groups-linkedin-scam/
https://www.linkedin.com/pulse/lazarus-groups-fake-linkedin-job-offers-malware-delivery-merton-uuk3c/
https://www.mcafee.com/blogs/other-blogs/mcafee-labs/lazarus-resurfaces-targets-global-banks-bitcoin-users/
https://blog.barracuda.com/2025/09/23/lazarus-group–a-criminal-syndicate-with-a-flag
NPM supply chain attacks
In recent years, supply chain attacks have emerged as one of the most significant security threats facing developers and organizations worldwide. These sophisticated attacks exploit the trust we place in third-party dependencies, allowing malicious packages to infiltrate projects through seemingly legitimate dependencies. The consequences can be devastating from data breaches and financial losses to complete system compromise.
As developers, we rely heavily on npm packages to accelerate our development process. However, this convenience comes with inherent risks. Malicious actors are increasingly targeting the software supply chain, creating packages that appear legitimate but contain hidden malware, wallet hijacking code, or other malicious functionality.
https://www.aikido.dev/blog/npm-debug-and-chalk-packages-compromised
